Security researchers from both UC Santa Barbara and Georgia Tech have discovered a set of Android vulnerabilities which would allow a hacker complete control of your devices. The scary bit? Apparently the would-be hacker can attack your devices even when locked and the screen is switched off.
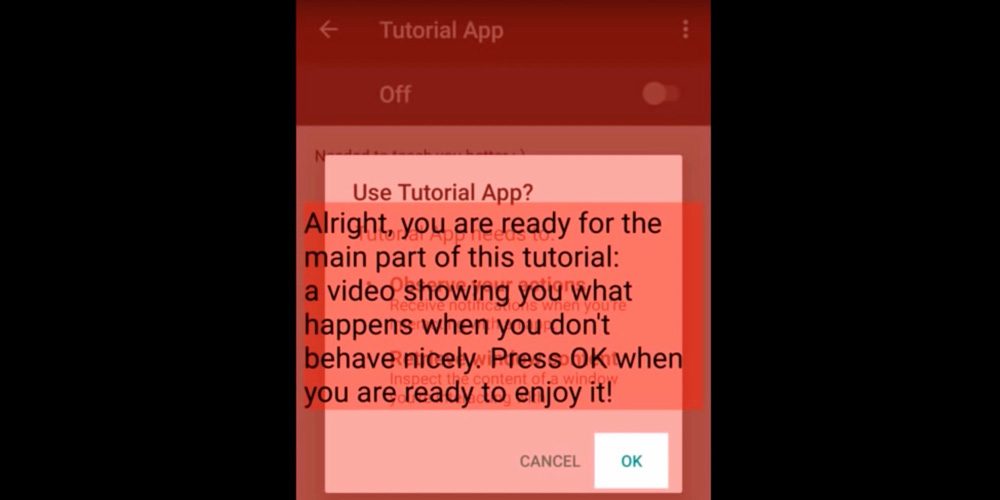
The image above shows one attack vector called ‘clickjacking’. The user innocently thinks they are agreeing to go through a tutorial, whilst invisibly behind the scenes (within the notification and app as a whole) they unwittingly ‘approve’ the hack.
The researchers, for illustrative reasons, have made the real action or hack, visible behind the overlay public. However in real use (as per the video further below) the permission box would be invisible to the user.
These attacks allow a malicious app to completely control the UI feedback loop and take over the device — without giving the user a chance to notice the malicious activity. These attacks only require two permissions that, in case the app is installed from the Play Store, the user does not need to explicitly grant and for which she is not even notified. Our user study indicates that these attacks are practical. These attacks affect all recent versions of Android (including the latest version, Android 7.1.2), and they are yet to be fixed.
The researchers disclosed their findings to Google, which has acted swiftly to update Google Play Protect to prevent installation of apps which take advantage of this vulnerability (via Engadget):
We’ve been in close touch with the researchers and, as always, we appreciate their efforts to help keep our users safer. We have updated Google Play Protect — our security services on all Android devices with Google Play — to detect and prevent the installation of these apps. Prior to this report, we had already built new security protections into Android O that will further strengthen our protection from these issues, moving forward.
However, the researchers have pointed out that the Google update is only a stop-gap measure at best:
Google implemented a partial fix (only on Android 7.1.2): “on top” overlays do not appear anymore whenever an app’s permission list is shown. However, this is only used for “normal” permissions, and not for “special” permissions, such as “draw on top” and a11y. This is problematic: since the “clickjacking → a11y” is still possible, a malicious app can use the “Phone Unlocking (while keeping the screen off) attack” to enable these permissions while keeping the screen off, thus making the silent installation of a God-mode app still practical.
Thus, while Google has moved quickly to head off some of the vulnerability, the attacks described in their original report remain practical and relevant, and a risk to Android users until a more substantive fix is developed. To get a better understanding of the issue, you can watch a video below showing you the hack and what it can do to your mobile device: