Koushik Dutta, who you might remember from such popular root applications as ROM manager, Carbon Backup, as well as the ClockworkMod Recovery, has just today released his own, open-source superuser application to the Play Store. I can hear you asking now, ‘Why would I want yet another superuser application on my Android device?’ Well, let me give you Koush’s response to that exact question:
- Superuser should be open source. It’s the gateway to root on your device. It must be open for independent security analysis. Obscurity (closed source) is not security.
- Superuser should be NDK buildable. No internal Android references.
- Superuser should also be AOSP buildable for those that want to embed it in their ROM.
- Superuser should also be AOSP embeddable, meaning a ROM can easily embed it into their Settings app.
- Maintenance and updates on both the market and source repositories should be timely.
- If something goes wrong, I can fix it.
- Handle multiuser (4.2+) properly
- Handle concurrent su requests properly
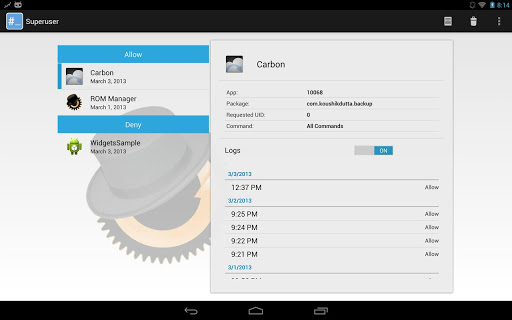
Koush’s Superuser application installs from the Play Store, and if you already have root access, after your confirmation, it will remove any other su binary and superuser.apk from your device, installing itself in its place. If you don’t already have root access, the application will download an update.zip that can be flashed through recovery. The UI is lovely, and it supports 7 and 10-inch tablets, but perhaps more impressively is that Koush is pushing for applications to declare a request for superuser access in their manifest. This means that when downloading such an application from the Play Store, users will be warned that the application requires superuser access, and Koush’s Superuser allows you to only allow root access to applications that explicitly request it in their manifest.
[app]com.koushikdutta.superuser[/app]






It’s great, works well.. but does it last after a cyanogenmod nightly update? I was under the impression that the nightlies always installed the original superuser over the top of whatever was currently installed.
That would be right Adrian; if you install a new nightly (i.e. a new /system image) then you’ll bomb out whatever was there before that, including any superuser binary installed by a Play Store app like this one.