If you’ve been on the internet in the last week, you’ve probably read about the vulnerability found in OpenSSL which affects a good percentage of the Internet. Heartbleed is the name given to a vulnerability in Open SSL, the secure sockets layer software for secure internet transactions (e.g. web servers running on https, like your bank, or our donation portal). It allows a would-be hacker to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.
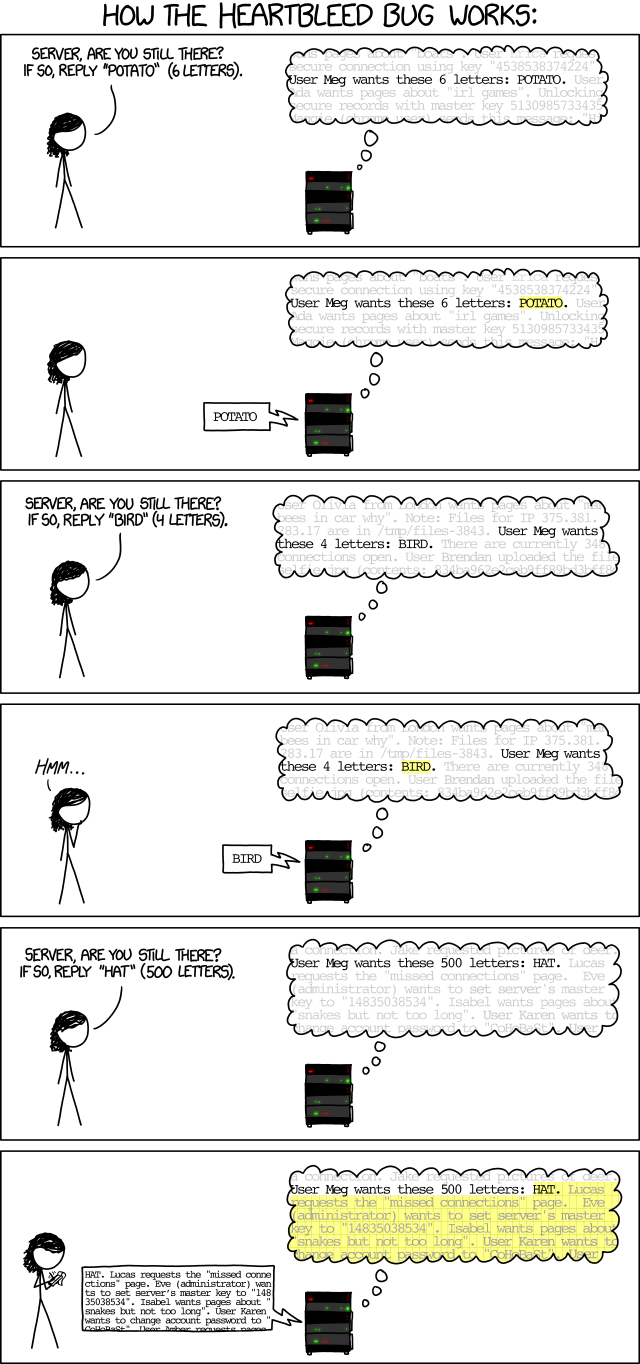
For those who don’t quite follow, XKCD have published an awesome comic today that shows the issue quite clearly:
We ourselves have been affected by this, having to upgrade the SSL software for the Ausdroid Community Foundation and have our server certificates reissued to protect against any possible issues. We’ve not identified any compromised information, but we can’t be too careful.
While the majority of the concern lies on the server side of the Internet equation, there are concerns that some client software might be vulnerable as well, although the risk is much, much smaller due to the client side being generally considered much harder to compromise.
In Android land, we’re pretty safe. It seems Heartbleed is only causing issues for one specific version of Android — Android 4.1.1. Every other version is, according to Google, immune to the vulnerability.
The downside, of course, is that devices running software this old might not actually receive an update. It would require a code fix from Google (which has been done) and also an update then being pushed out to affected handsets by manufacturers and carriers, and we all know how difficult that process can be.
It’s not immediately clear just how many handsets could be affected, but we do know a little. According to the numbers coming from earlier this month, Android 4.1.x currently accounts for 34.4 percent of Android usage. We can only hope the patching update rolls out quickly, and that Android 4.1.1 makes up a small percentage of the overall Android 4.1.x figure.
Failing that, if you’re a user with a 4.1.1 handset and you’re especially concerned that your handset could be vulnerable, if an update isn’t forthcoming, upgrading to a different handset might be the only option.




This vulnerability only applies to TLS servers. Unless your phone is running some sort of secure server (such as an SSH server, SFTP server, etc) you have nothing to worry about.