An Australian Tax Office (ATO) staffer has been disciplined after leaking a powerpoint slideshow to social network LinkedIn relating to internal processes from the department on how to retrieve information from mobile phones.
The document, now removed, was hosted on slideshare, and detailed how to ‘bypass passwords and obtain data even if the phone battery is flat and does not have a sim card’ as well as ‘how to retrieve deleted data, access text messages and phone call records’ according to a report from the ABC.
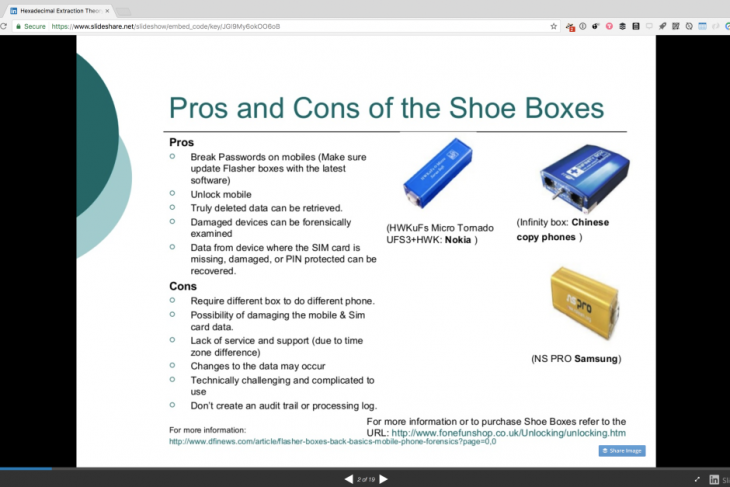
The report leaves more questions than answers on how this hacking was achieved. A slide from the now removed document shared by the ABC shows a pros and cons list related to using so-called off the shelf ‘shoe boxes’ a cursory tech used to unlock phones to some extent. The extent of the ‘hacking’ is somewhat minimised with the highlighting of a shoe-box used to access Nokia devices, presumably older style devices, not the as-yet to be released new devices from HMD Global.
The phone unlock method using shoe boxes is available to almost anyone through places such as the UK-based fonefunshop website shown in the slide. The report does quote Troy Hunt, a Microsoft regional director and security researcher, who said that ‘the instructions were dated’, he further went on to say that he was surprised that the ‘ATO were sharing that level of technical advice’.
When approached for comment, the ATO, through a spokesperson said
Phones were only accessed with a warrant under the Crimes Act, or with written consent from the owner.
The article shows that the ATO at least, is moving towards acquiring methods to retrieve data from mobile phones. This revelation is somewhat benign for the majority of users using updated devices with the latest security patches, highlighting the need to keep phones up to date. For the majority of Australians though, an up to date mobile phone or even a current generation mobile phone isn’t a priority showing that the data required by the ATO is a simple step from accessing.
More advanced devices may require the use of third party companies such as Israeli company Cellebrite who last year were apparently used by the US Federal Bureau of Investigation to access a locked iPhone after Apple refused to help. Though that case did involve a fingerprint scanner, it also used an older version of iOS, and Cellbrite’s ability to access current generation Android or iOS devices with bio-metric security such as fingerprint scanners is currently unproven, at least publicly.