For at least two years now, discerning buyers have been migrating their hardware over to USB C for anything and everything possible. For around 12 months, a not insignificant number of buyers simply won’t buy hardware unless it’s USB C and now Yubikey have hit the nail on the head. The 5C NFC isn’t just USB C, it also sports NFC for fast touch authentication making hardware-based 2FA a no-brainer.
What is it?
Yubikey is hardware-based — in this case USB C with NFC — 2FA key that has far broader compatibility than many users realise. Everything from simple Windows or Mac OS logins, to protecting your online accounts. Yubikey has continually worked with a lot of high profile providers to offer a higher level of security to your important data.
What does it do?
Yubikey offers two-factor authentication (2FA) in hardware form which — despite the cost involved — offers increased security, as well as speed and convenience. Using the example of my Google account I enter my username and password, the system then requests 2FA by plugging in the key.
The 5C NFC offers an additional feature for the current generation of hardware, aside from the USB C connection terms of connectivity. That — clear from the device name — is NFC and it’s a dimension that I honestly didn’t realise could be this darn good.
What are the risks?
Let’s take a look at a simple example with Facebook, what would happen if your account was compromised?
Let’s start with a simple fact: Login with Facebook is hugely popular because it’s easy. But do you know how many sites you’ve got linked to your Facebook account? Do you know how many of those have your credit card attached to them? If you’re on Facebook, the odds are you’ve got Instagram which means messaging history, as well as potentially very sensitive private data, is exposed.
The search trends from Google show that with so many more users at home during the pandemic, the thought of accessing other peoples data is coming into play. Specifically the term “how to hack” has been on the rise steadily with Facebook, Gmail, email, Google and Wi-Fi heading the list.
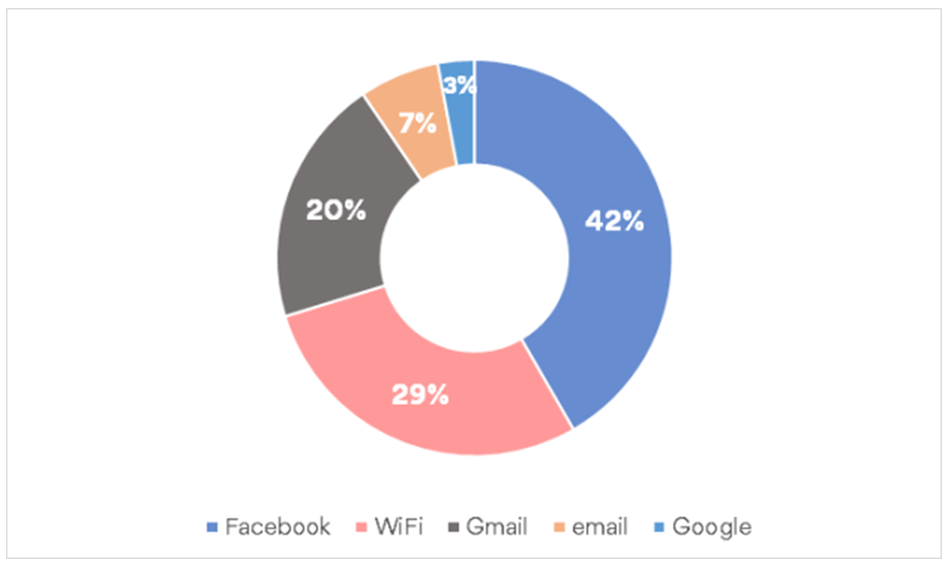
Hopefully, the need for any and all protection possible is starting to shine through.
Is the user experience worthwhile?
For my mind, this product isn’t just about the user experience with the device. But makes me think about about the — let’s be honest — terrible experience having it securing your accounts significantly decreases the chances of… account and personal data loss.
From talking to personal contacts, it seems there is a misconception that the 2FA keys generally only work with corporate accounts and niche offerings. Certainly not the case, if you want to see the ever-growing list of compatible offerings: Check out the Yubikey page to see just how many accounts you can secure.
There is of course some early work to be done to like the Yubikey to your accounts. This needs to be done one by one, which is — while quite simple — a little time-consuming. But back to my earlier point about the prevention of data loss, the reality is: If 2FA is offered on any of your accounts, you should be using it.
The fact is that using the Yubikey is simple and fast. Some would argue faster than loading an app for 2FA codes or waiting for them to be delivered via SMS and I agree. SMS or Email delivery of 2FA keys can take between a few seconds and several minutes. The use of 2FA apps like Authy or Google Authenticator is easy, is no more time-efficient than a hardware key and (while minor) has some minor flaws compared to a physical hardware key.
Once you’ve set up the key, there is a bit of adjustment to your normal workflow you’ll need to make. For me, that adjustment was as simple as adding the Yubikey to my keys which I carry anytime I’m out of the house and is within arms reach when I’m at the computer at home.
From there it’s just a case of grabbing your 2FA key when you’re prompted and either tapping it to the NFC sensor or plugging it in and touching the sensor.
Should you buy one?
Anyone that’s heavily security-minded probably already has one or is looking online for one now. Coming from an IT background and working inside some high level corporate, enterprise and health networks I tend to stress good security practice. In this case, whether it’s for personal use or within a corporate environment I can’t impress highly enough how important two-factor authentication is.
The quickest, easiest and frankly cheapest option is apps like Google Authenticator or Authy. They will 100% improve your security to your accounts, but no system is perfect. What the physical 2FA key from Yubikey offers is a quick and easy access pathway to ensure your data is secured as much as possible while minimising the impact on workflow and time lost.
In short, the US$45.00 (approximately AU$61.00) is well and truly worth the investment to protect yourself, your data and ultimately preventing you from a heap of headaches and heartache.
Disclosure Statement
The cost of the device makes its return impractical for the manufacturer who has not requested its return.








In my experience, you are more likely to have your phone with you than a physical key when working (I am an IT professional who works with a laptop and I work indifferent locations within my bulding or at home) so I would like to ask is the extra of security provided by a Yubikey worth it vs using 2fa with Authy? What is the extra security it offers specifically? Could you provide more insight for people who are already using 2fa and are contemplating the switch to using a Yubikey?
I’ve used Google Authenticator in the past and it was OK, but was really annoying when I changed phone handsets, as I had to set up everything again. That’s been the appeal of SMS 2FA to date. Yes it can be annoying waiting for the message to arrive, but it’s phone handset independent. But you’ve got me thinking that I really should invest in one of these.
One question though: how does something like Yubikey work for things like Apple TV or Roku or a Playstation where there is no ability to use NFC or a USB-C port?
I use a usb-A yubikey. For things like playstations etc they don’t generally support u2f authentication, so they require the generation of one time codes. Due to the NFC you can do this by simply tapping your yubikey on the back of your phone, this opens the yubikey app and generates you codes. (You might need to tap twice?). For apps and sites that support u2f (like GitHub etc) instead of asking for one time codes, simply tapping the NFC device to the phone or inserting it into USB on my PC and tapping the symbol is enough to authenticate… Read more »
I had the same issue so I moved from Google Authenticator to Authy. You can sync between multiple devices which allows your setup between phones.
I am starting not to like SMS 2FA for the fear of someone stealing/transfering my phone number away and having access to that SMS 2FA, so where available I am trying to use one one time codes instead of SMS 2fA.
https://authy.com/blog/authy-vs-google-authenticator/
This is why I use Authy, it primarily attaches to your phone number and is cloud backed so that on a new device is as simple as logging in.