Look, this shouldn’t really come as a surprise; if you allow Google to record your location history, there’s half a chance that it could be produced to a 3rd party with a court order, and that includes law enforcement. The feature is quite useful for individuals – allowing you to see where you’ve been, how far you’ve traveled, etc – but for law enforcement in the US, it seems like it’s a growth industry.
In an eye-opening story published in the New York Times, they’ve explored how law enforcement in particular have used the location history service to some surprising ends.
For example, knowing that a crime was committed in a particular place at a particular time gives some parameters which are very helpful. Given that a large percentage of Android phones log their location with Google every so often, it doesn’t take a huge stretch of the imagination to see how law enforcement could define a time range and a geo-fence and ask Google to identify who was in that space during that time.
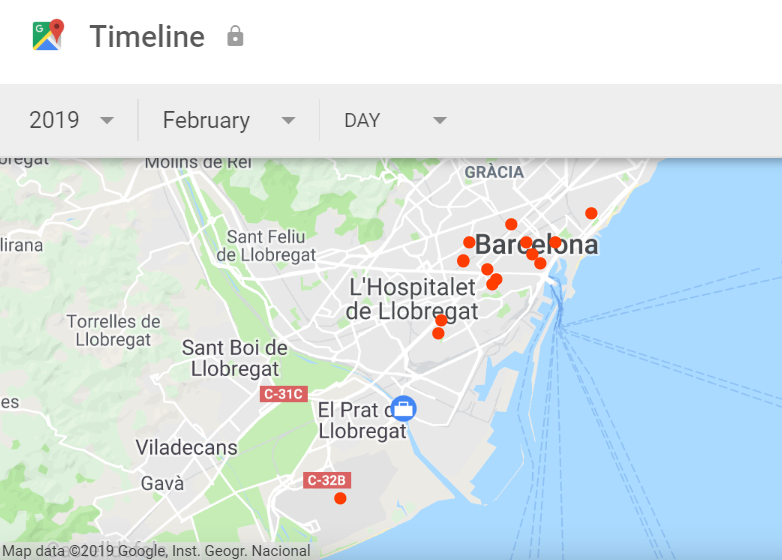
That’s precisely what law enforcement agencies in the US have been doing, and not only to locate potential suspects, but also to identify potential witnesses too.
Typically done under a search warrant – a kind of written authority for law enforcement agencies to take property (incl. computer records) from some body or company – these kinds of searches are in their infancy, but proving quite helpful in solving otherwise difficult crimes.
Google has a bit of a history in trying to keep user data confidential where it can, but it’s difficult to resist a properly framed search warrant, so Google has done its best to minimise the information disclosed. It uses a two-phase system whereby an ID number is generated for each user that would be caught up in a geo-fence warrant, and the law enforcement agencies narrow down particular identifiers of interest. Only for those particular IDs selected are further details disclosed.
It’s not much, but it’s something.

It’s unclear whether this kind of search warrant is being used in Australia, but Google’s Sensorvault (as the data store is known internally) is just one of many tools ‘available’ to law enforcement here. We’ve already got pretty onerous metadata retention laws which law enforcement agencies can access fairly readily, and it’s academic for agencies to access subscriber data and other information from telecommunications providers as well. Sometimes, all it takes is a brief letter with a reference to empowering legislation, and boom, your info is handed over.
What’s the lesson in this?
If you’re going to commit crimes, obviously, you’d do well to make sure you’re not handing identifying information away to all and sundry. Turn your phone off and leave it at home perhaps. For everyone else, though, this is a cautionary tale – just because Google has a privacy policy and you think your data might be somewhat secure doesn’t mean that it can’t be lawfully accessed in ways like those described in this story.
If this sends a shiver up your spine – it did for me – it might be worth looking into how you can disable and delete your Google Location History.