Some online services make it fairly difficult to secure your account beyond an email address and a password. When you stop and consider just how much of your online identity is protected by these two simple things – which are also quite easy to steal – you’d be a little worried.
Two factor authentication (2FA), or sometimes called two-step verification (2SV) is probably the best way to protect your online accounts, as it requires something you know – your password – and something you have (a secure code generated by your mobile, a security token, etc). However, for some people, the inconvenience outweighs the security benefits, and so they don’t use it.
However, there are simple steps you can take to protect yourself online without causing extra inconvenience.
9to5Google reports that Google worked with New York University and the University of California, San Diego on a year-long study about wide-scale and targeted attacks. The high-level conclusion is that any form of additional security challenge can significantly prevent account hijackings.
Our research shows that simply adding a recovery phone number to your Google Account can block up to 100% of automated bots, 96% of bulk phishing attacks, and 66% of targeted attacks that occurred during our investigation.
With your Google account (at least) there’s half a dozen challenges that can be deployed when your account is accessed in a suspicious way (e.g. from a public internet terminal, from a country you’ve never been to, etc), which include:
- An on-device prompt*
- An SMS code
- Security key*
- Secondary email address
- Phone number
- Last sign-in location
Those marked with an asterisk require you to set something additional up, but the other options are available to virtually all accounts, provided you’ve specified a secondary email address or your mobile number. As you can see, those additional steps prevented 100% of automated bot-based account attacks, and – in most cases, at least – bulk phishing attacks too. With the exception of last sign-in location, all were fairly effective at blocking targeted attacks too.
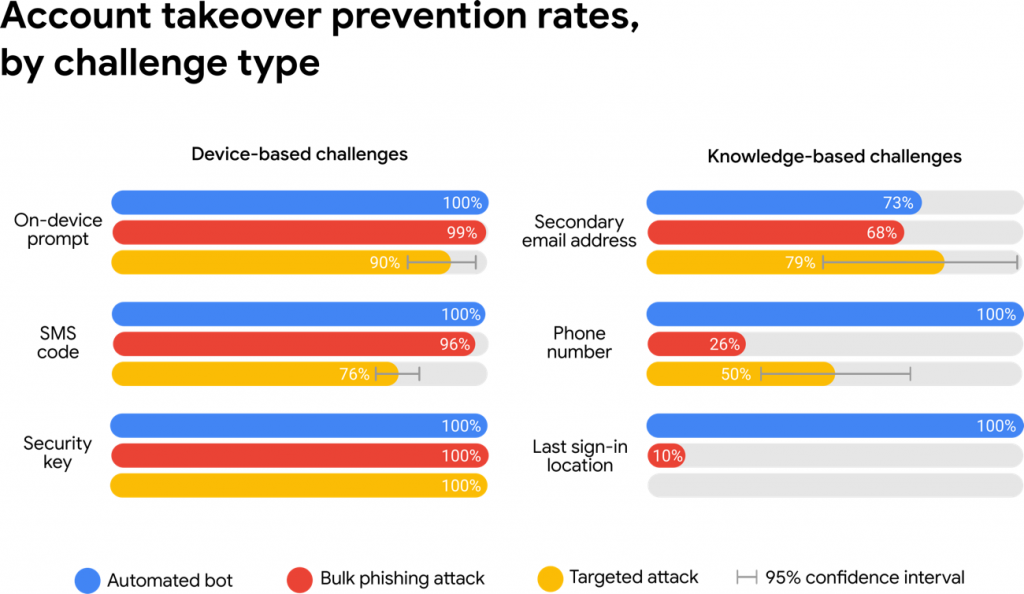 Obviously some sort of physical authentication is the gold standard here – something you must have in your possession in order to access your account. Whether it be a security key (which was 100% effective), an on-device prompt (which was almost as effective, unless someone’s pinched your phone) or an SMS code (the same caveats) you’re almost guaranteed to be pretty safe.
Obviously some sort of physical authentication is the gold standard here – something you must have in your possession in order to access your account. Whether it be a security key (which was 100% effective), an on-device prompt (which was almost as effective, unless someone’s pinched your phone) or an SMS code (the same caveats) you’re almost guaranteed to be pretty safe.
Google’s research did discuss the barrier to setting up these kinds of challenges, though:
The answer is that challenges introduce additional friction and increase the risk of account lockout. In an experiment, 38% of users did not have access to their phone when challenged. Another 34% of users could not recall their secondary email address.
The findings also detailed the emerging trend of “hack for hire” attacks. Most users do not face this risk, but Google recommends that high-risk targets sign-up for the Advanced Protection Program:
We have been investigating emerging “hack for hire” criminal groups that purport to break into a single account for a fee on the order of $750 USD. These attackers often rely on spear phishing emails that impersonate family members, colleagues, government officials, or even Google. If the target doesn’t fall for the first spear phishing attempt, follow-on attacks persist for upwards of a month.




