It’s a fact of life, we’re becoming more critically reliant on our mobile phones to run our daily lives. This does two things, makes them more valuable to us and makes them a significant target for cybercrime. It’s this second point that makes the fact that the Triada Trojan being found pre-installed on a number of Android devices in 2017 very concerning for users.
Kaspersky have an excellent wrap of of the Triada Trojan and how it has come to be installed on so many low cost Android devices.
The Triada Trojan first tries to collect some information about the system — like the device model, the OS version, the amount of the SD card space, the list of the installed applications and other things. Then it sends all that information to the Command & Control server. We have detected a total of 17 C&C servers on 4 different domains, which probably means the bad guys are quite familiar with what redundancy is.
The C&C server then responds with a configuration file, containing the personal identification number for the device and some settings — the time interval between contacting the server, the list of modules to be installed and so on. After the modules are installed they are deployed to the short term memory and deleted from the device storage, which makes the Trojan a lot harder to catch.
There’s a lot more to it, so well worth a read of the site if you’re interested.
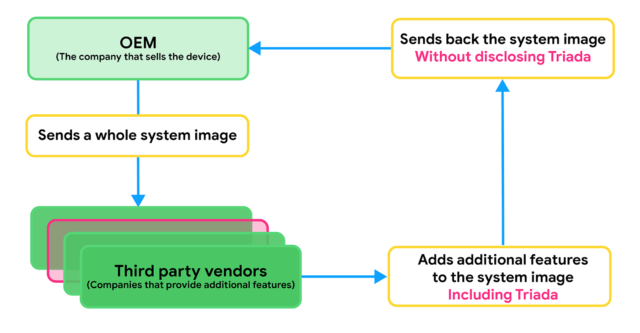
The delivery was pretty elaborate, involving third party infection during production process and final delivery of the firmware that will be installed on the hardware. It shows the lengths that cybercriminals will go to, in order to gain access to your personal data. This could be as simple as email or social media accounts, or as complex as using 2FA to gain access to your bank accounts.
Sadly there are many ways to gain access to all of your data including simply porting your mobile phone number to get your SMS 2FA access as one of my former work colleagues found out. Ultimately the best protection you can have it to be vigilant, use strong passwords, a password manager and use 2FA everywhere that it is available.





Has this been found on any devices sold here in Australia?