Epic Games’ decision to distribute Fortnite outside of the Google Play ecosystem was bound to get people’s attention, and though I earlier said this probably wouldn’t cause issues, it seems I wasn’t entirely right. A technical vulnerability was discovered – by Google, no less – and patched fairly well immediately by Epic. To date, there’s no information to suggest the vulnerability was actually exploited by anyone, given it wasn’t publicly discussed until it was fixed, but who knows.
What was the vulnerability?
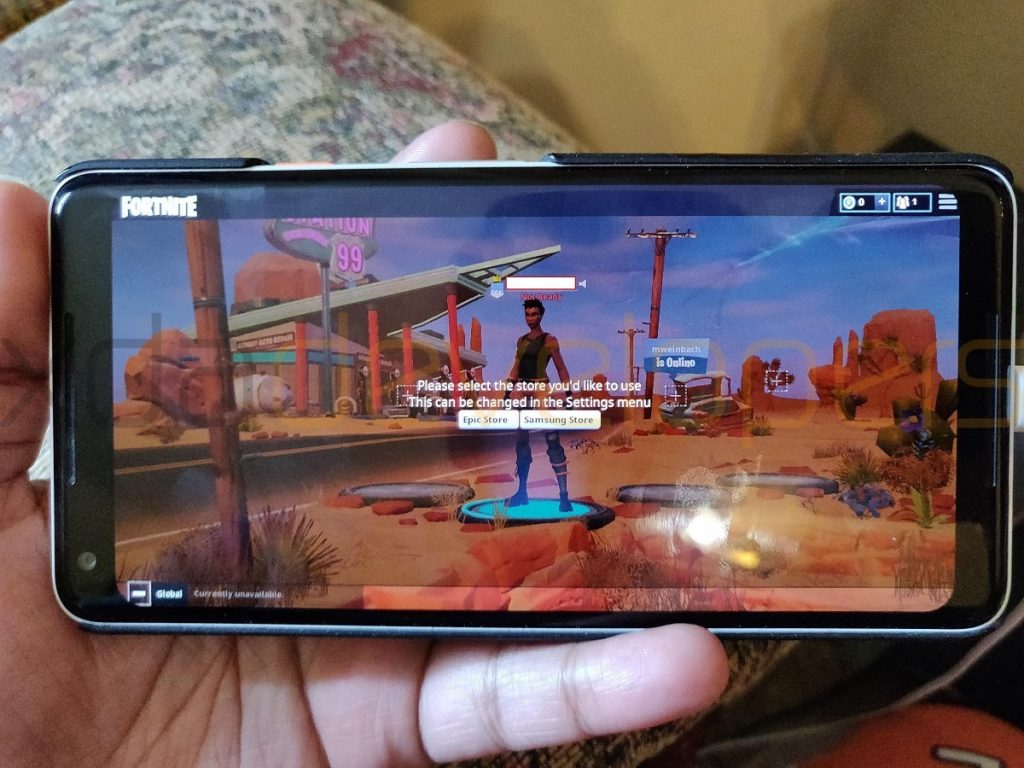
As discussed earlier, Fortnite doesn’t download from Google Play. Rather, users download Fortnite’s installer from Epic’s website, and that installer app in turn downloads Fortnite. Nothing really exciting about this, except that there was much kvetching in the tech-nerd space about what a poor decision (or a greedy one, perhaps) this was on behalf of Epic.
The vulnerability came about because Epic had been a bit careless about how it handled the installation of its primary game; due to the size of the downloaded app, no doubt, it is downloaded to External Storage before it is then installed by the Installer service.
This leaves the process open to exploitation; a malicious app could insert its own APK file into the process stream, and trick the Epic Installer into installing said APK.
If this occurred, that malicious app could install silently, without notice to the user, and (likely) with full permissions, regardless of Android’s permission model. You trusted the installer, so you trust whatever it installs. Some say this means Epic’s process is broken, but if you ask me, this is a bigger problem and something that Android probably needs to address, too.
Did it matter?
Arguably, but probably not. For this vulnerability to have even a remote chance of being exploited, a user would have to have both (a) installed the Fortnite installer and (b) installed some other malicious app which was specifically designed to exploit the vulnerability in Fortnite’s installer.
Let’s stop for a moment.
Most users do not install apps from outside the official Google Play store process, and those who install Fortnite make an exception to that generalisation. However, they would need to have either (a) installed some other malicious app from outside the Play Store, or (b) been unlucky enough to install some malicious app from Google Play which somehow missed being detected by Google’s pretty capable malware scanning process.
In short, it’s a fairly remote possibility at best.
So, while not a great vulnerability to have put out in the wild, it’s one that doesn’t seem terribly likely to have been actually exploited.
What’s the rub?
Fortnite players probably don’t need to panic. There’s a new Fortnite Installer out (version 2.1.0) and chances are you’ve already got it. If you don’t, open up the Installer, hit Settings and check for a new update.
If you don’t have the new version, I’d suggest you install it now.
You should also check your Google Play Protect settings to make sure you’ve got scanning turned on; if you do (and have done), chances are anything which might’ve exploited Fortnite’s installer would’ve been detected and dealt with before you even read this article.




And this is why you distribute your Android apps through the Play Store.
I agree – though, evidence wise, a single low-stakes, fixed vulnerability is not by itself worth a 30% loss of income to Epic.
We’ll see if more occur though + issues with ppl being duped by fake download sites (which is my theory of why it’s a bad move).