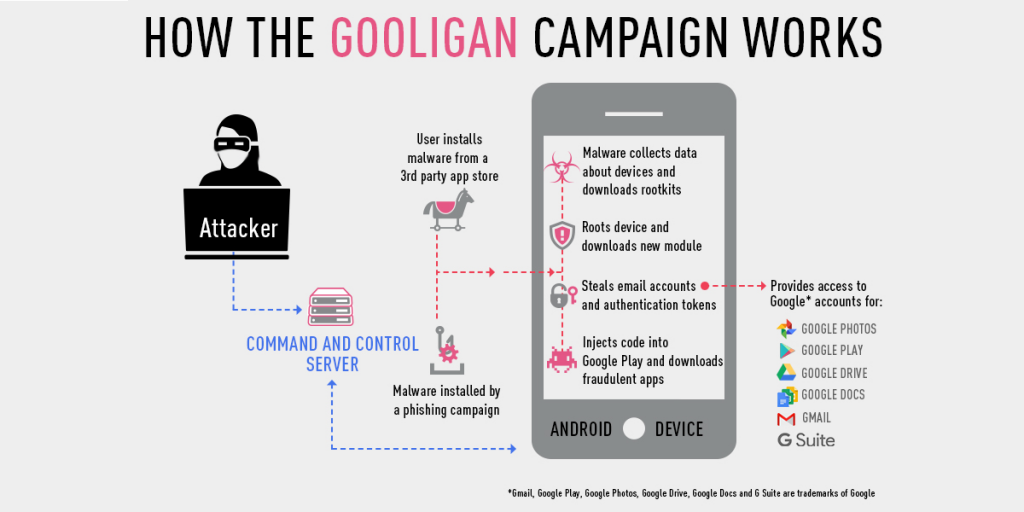
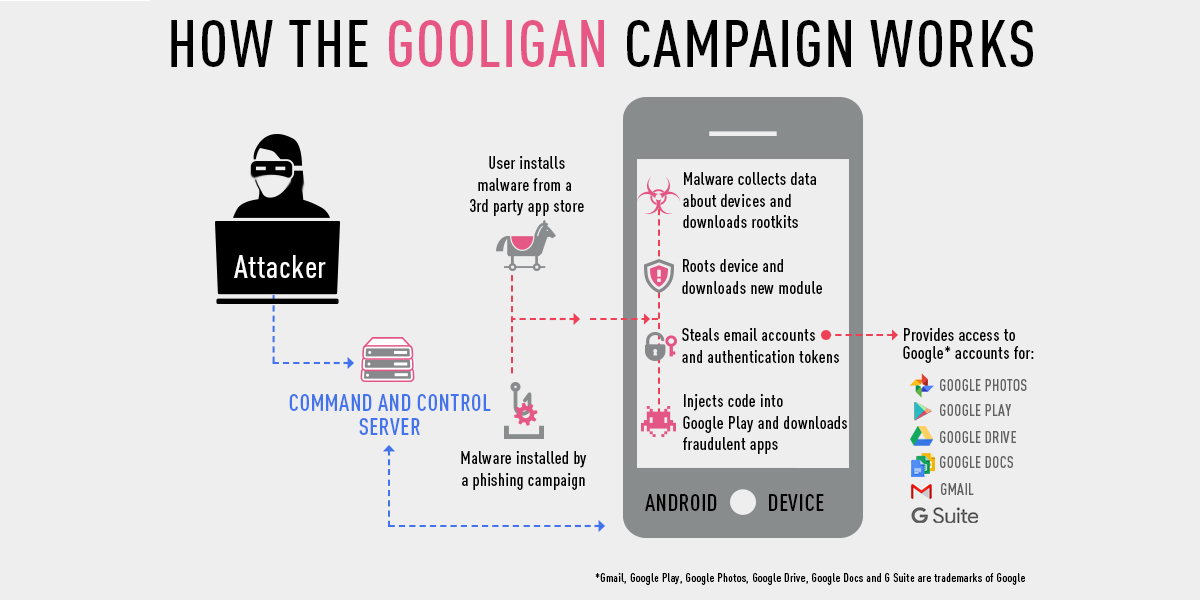
In a rather alarming statistic, Check Point Research has revealed that Android malware by the name of Gooligan has gotten around and breached upwards of a million Google accounts, and this figure is reportedly increasing by more than 13,000 accounts per day.
If you only use the Google Play Store to download apps and games, chances are your phone is safe. Also, if your phone runs Marshmallow or above, your phone is safe. If you’ve used a 3rd party app store, or downloaded apps from other potentially unsafe sources, you may well have been at risk, or worse, installed a Gooligan-infected app.
The vector for Gooligan to infect your phone is the same as most other Android malware; a user has to install an infected app from somewhere, and invariable they come from sources other than Google’s Play Store. Pirated apps are ripe for this kind of thing, as are unofficial, third party app stores which might offer paid apps for free download. Basically, if it looks too good to be true, you’re mad to install it on your phone.
Once installed, Gooligan can do all sorts of things, including collecting data about your phone, rooting your phone, and stealing your email accounts and authentication tokens (which gives them theoretical access to all your Google apps — like Photos, Drive, and Docs).
It gets worse, though. Gooligan can inject code into the Google Play Store which causes it to download infected, fraudulent apps. This makes those behind Gooligan a lot of money, because those hacked phones download and display ads inside fake apps, which unwitting users might not even know aren’t the real thing.
From what we understand from Check Point’s research, the majority of breached accounts are concentrated in Asia, but as many as 28% of them are located in the Americas and Europe. To see if you’re compromised, head to the web site that Check Point created: https://gooligan.checkpoint.com/.
Unfortunately, this highlights one of the problems we’ve spoken about before, and with Android’s significantly more fragmented software experience (compared to the Apple-controlled iOS), there’s a lot of devices out there running older software which will never be updated to protect against things like this. With ‘safe’ versions of Android only on about 26% of phones as of last month, that still leaves 74% of Android devices potentially able to be infected and exploited. Of course, there’s a lot of other things that have to happen before an exploit can actually take hold, but such a high percentage of potential targets is worrying enough.
There is a silver lining, though. Even on older devices, Google’s “Verify Apps” feature is rather frequently used. Google hasn’t released specifics on what percentage of devices use the feature, but Check Point believes that up to 92% of active Android devices use this feature.
Even apps that aren’t downloaded from Google’s Play Store can be checked against Google’s database of known dodgy apps. The first time a user tries to install an app from a non-Play Store source, the user will be prompted to allow Google to verify the app, and in our experience, a good many users happily click Yes to this, thinking it enhances their security — and it does.




Why I never install apps from a third party unless I am really sure of it, or upgrading an existing app.
This shouldn’t really affect most users in Australia, especially the non techy ones.