Public Service Announcement
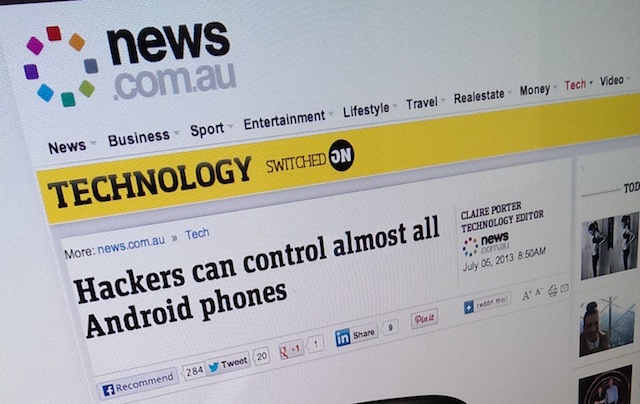
Today, News.com.au Technology Editor Claire Porter claimed that almost all Android phones are vulnerable to hacking or being completely taken over remotely by cyber criminals. In this alarmist, and almost completely inaccurate news story, Porter claims:
Cyber criminals wait for legitimate apps to be approved for sale, and then go in and modify the code after and create an exploit that allows them to take over people’s phones by an app.
This simply isn’t true. This implies that cyber criminals are, in some way, able to get into apps that are approved for sale via the Google Play Store, and insert trojan code into these which will then take over user’s phones. Not only is this remarkably unlikely (and not detailed anywhere in the source story on BlueBox’ blog), but any app containing this trojan code that was uploaded to the Play Store will be detected by Google and prevented from being published. You can see our story on this exploit yesterday for more detail on how this works.
In brief, Jeff Forristal, Bluebox CTO explains that when a developer initially uploads an App to Google Play for approval, Google scans the files digital signature and records it. Subsequent updates for the App are scanned against this signature for aberrations. Google has actually updated the Google Play Store application approval process to specifically look for this exploit and remove the possibility of it affecting users, at least for app updates in the official store.
So far it appears though this flaw only affects non Google apps, considering the amount of third party apps that exist in the Google store that’s hardly a paltry number.
This flaw only affects apps that are distributed through channels other than the Google Play Store. From what Ausdroid knows, and from what information about this exploit there is publicly available, no app that is uploaded to, and subsequently downloaded by users from, the Google Play Store can infect a user’s phone with this exploit. Only APK files (Android’s application file format) that are downloaded from other sources, such as directly from web sites, or potentially third party app stores, are potentially vulnerable.
We repeat. The Google Play Store mechanism detects and prevents any APK containing this trojan code from being uploaded. It doesn’t effect “all third party apps”.
Well, the news isn’t good. Until further notice, news.com.au recommends that you don’t download any non-Google apps.
This is just an overreaction. Ausdroid believes, and has seen many sources stating, that any app you download from Google’s Play Store will be free of this vulnerability. Why? Because Google are aware of it, and have ensured that the Play Store detects and prevents any apps containing this vulnerability from being uploaded or made available.
You need only be careful downloading apps from third party sources, such as direct from websites, forums or questionable sources, though of course, you should be careful downloading apps from those sources anyway, as you do not benefit from Google’s Play Store protections.
Also, if you have any apps which store your personal information such as credit card or PayPal information (like eBay, Amazon or Etsy), you should remove this information immediately. Remove any personal information from your phone (do you have your credit card pin stored in your notes? Get rid of it).
Apps like eBay, Amazon, and Etsy do not store your credit card or PayPal information on your phone. Rather, this information is stored in these companies’ online services, which your apps access. Removing all these apps is probably an overreaction, but if you are concerned, by all means remove them.
The last point — removing personal information from your phone — is a good way to make your phone fairly useless, and is probably an overreaction as well. Keeping your credit card PIN stored in notes on your phone is a remarkably bad idea, regardless of the existence of any vulnerability.
Ausdroid does recommend, however, that you do not leave the ‘Allow installations of apps from sources other than the Play Store’ ticked. This will prevent any third party apps from being installed unless you specifically allow it to occur, this offering you some further protection. I think that’s one part of the story we can all agree with.




We’ve had our fun with the comments on this thread, and they’re now closed.
From the CIO story – ” However, if an attacker tricks a user to manually install a malicious update for an app originally installed through Google Play, the app will be replaced and the new version will no longer interact with the app store.” Source CIO. Chris, the story where you lifted all your information from says the above. So isn’t it a bit of an overreaction from you to say Google Play Store is totally safe. I know you are a fanboi but try and show some balance. This is a major flaw. All your readers use Android phones,… Read more »
Reg, we read the CIO story (and the Blueboxx story) quite carefully before we posted our original story, and before we pointed out the flaws in news.com.au’s story as well. Trust me, we were very careful in posting these two stories, as we don’t want to set a cat amongst the pigeons, so to speak. If you only install apps from the Play store, and by implication, only update your apps through the Play store, you are safe. It’s as simple as that. Sure, if an attacker convinces you to install an update to a Play store app from a… Read more »
Chris wins the internet with this article. I was astounded by the amount of inaccuracies in the news.com.au article. I wonder if they actually did any research themselves?
Funnily enough , and coincidentally i am sure, the company who did the research also have a security suite for sale… :-/
news.com.au would easily have to be the worst source of news available in the country. I have a room mate who gets 90% of her news from that site, which thankfully is mostly celebrity gossip, but occasionally it’s some dangerously sensationalistic crap that is completely untrue, based off some skim read of another sensationalistic article elsewhere. She then proceeds to “alert” everyone of her “discovery”. It is f**king annoying, and I have to sound like a know-it-all every time I tell her she’s wrong. She doesn’t like being told she’s wrong, but she gets all her news from news.com.au and… Read more »
Great article, Chris. I’ve got a good mind to link this to that news.com.au article so their readers can have an alternative and (very) sensible point of view on this hacking story.
I sent her a message through her own webpage linking to this story and letting her know what I thought of her propaganda writing. If other people feel as strongly about this as me I suggest you let her know too, http://www.claireporter.net/contact-2/
News Limited loves Apple, so expecting them to be neutral towards anything not Apple, let alone expecting sane and competent writing from them, is like expecting a banana to do a tapdance.
What an ignorant piece of drivel from news.com.au. For normal people who download apps only from trusted developer’s websites, the only way this vulnerability will affect them is if the website they are downloading from is hacked and a legitimate app is replaced with an infected one. Given that, this vulnerability will probably have a pretty low impact in the real world.
what a collection of cretins
Its news.com.au. (News Ltd). almost 90% on there is sensationalist articles. The remaining 10% is bagging Labor!
Bagging labor is good though.
Excellent article, Chris!