
It’s been a little over two weeks since Android’s Stagefright vulnerability came to light. In that time, a number of OEMs have announced or released patches for some of their devices. Zimperium Mobile Security, the company behind the original discovery of the problem released, and then updated, an app to tell you if your device is vulnerable.
So at this time the questions many Android users have been asking are: “Am I at risk?” followed closely by “What do I need to do?”
We have delved deep into the murky waters of the Stagefright swamp in an attempt to provide some answers to those questions. To be clear, the Stagefright exploit is indeed a real risk to some Android devices and should not be simply dismissed as “not my problem”. Digital security is just as important as the locks on your doors or the PIN to your ATM card. That said, we will attempt to cut away the hype and media buzz to give you an honest picture of the risk.
What is Stagefright? Why does my phone have it?
Stagefright is Android’s core OS level Audio and Video decoder. It’s found in all versions of Android from its introduction in 2.2 and above. It is the thing that actually turns bits of data into sounds that can be played, and videos that can be watched, so it’s essential to the functioning of your device. Because of its duties and responsibilities, it runs with an elevated permission state (so it can access more parts of your phone than the app you just installed from Google Play).
It is also perhaps one of the most unfortunately-named parts of the Android OS, considering recent developments – Stagefright is a name just waiting to become something scary.
If you’re interested, this is Stagefright:
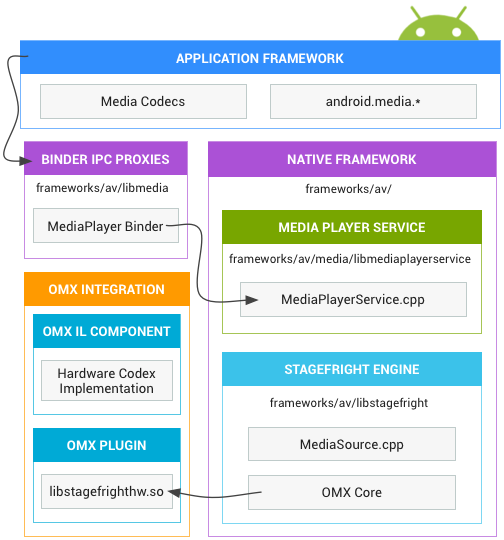
What is the Stagefright exploit? How could it be used?
Security researchers at Zimperium discovered a series of bugs in Stagefright’s media decoder that could be used to inject and execute malicious code. Even without specifics, that’s bad. Josh Drake from Zimperium rightly says, “You only need one bug to write an exploit”.
Because of the elevated access rights granted to Stagefright, it potentially has access to parts of OS that could be used to cause harm to your device and it’s those permissions that could be used by an exploit to do bad things to your phone.
The way in which a potential attacker could use the exploit to access your phone, or “attack vector”, could be any media content. Anything could contain malicious code that targets one of these known vulnerabilities, and when it’s passed to the Stagefright decoder the exploit code could run and do anything. It is this method of potential distribution that makes Stagefright a bigger deal.
The scary part is when you consider that MMS or IM programs typically receive media files and pass them to Stagefright without you knowing, so that when you open the app the image is there. If you were to receive an MMS containing malicious code that uses Stagefright exploits you might not even know it as the code could delete its own message and set about doing other things to your phone. You may not even know the attack happened.
Am I protected?
The ultimate protection to these bugs is a software update that patches the vulnerabilities the security researchers have found. To keep up to date with which OEMS have announced or released patches, you can check back with our Stagefright Hub.
As of now we’ve heard from:
What is Google doing to protect me?
Google has developed a patch and released the code to the Android Open Source Project (AOSP), so OEMs and ROM developers worldwide now have access to the patched code for Stagefright. As above Google has also released OTA updates to patch Nexus devices.
Adrian Ludwig, Lead Engineer for Android Security took to Google+ after the Stagefright vulnerability became public to discuss Android security in general. Taking issue with Zimperium’s assertion on bugs and exploits, he commented “There’s common, mistaken assumption that any software bug can be turned into a security exploit”.
Talking to NPR in the USA and writing on his profile, Adrian has responded to the Stagefright vulnerability with clarification regarding the security features Google has been building into Android to prevent the likelihood of a successful malicious attack – like one that would use a Stagefright exploit – on an Android device. He provided a link to all of the security improvements in Android since 4.0 that have been implemented to protect the Android OS from any bugs lurking in the system and preventing them from becoming a security exploit.
Address Space Layout Randomisation
The big ticket item that he focused on is a security feature know as Address Space Layout Randomisation or ASLR. In basic terms, ASLR randomly hides the location of Android System functions that an attacker would need to access to execute their malicious code. With ASLR, the system randomly assigns programs to a different section of RAM each and every time. Because of this the attacker would need to correctly guess the exact location of all of the systems they needed to access to execute their exploit on an affected device. This is akin to the proverbial needle in a haystack. ASLR was introduced in Android 4.0, and as such offers a layer of protection against the type of memory exploit the researchers were outlining.
Unfortunately, this still leaves devices between Android 2.2 and 4.0 vulnerable with no mitigation from ASLR. The latest Android distribution numbers place that at around 4.9% of all monthly active devices.
If Stagefright is a murky swamp, then ASLR security research is a rabbit hole from which one may never escape. You will find both proponents and opponents of ASLR within the digital security field. Your acceptance of this security measure will most likely come down to whether or not you trust Google’s interpretation of the issue. Google is touting that 90% of Android devices are “protected” from the issue, but has still seen fit to patch the bugs urgently.
What else can I do?
Some of the best advice at the moment, if your device is vulnerable, is to disable auotmatic retrieval of MMS messages. Once disabled, only open MMS messages from people you trust.
As Chris discussed in a previous post:
Protection against the SMS/MMS attack vector might be fairly trivial, depending on which SMS application you use.
- If you use Google Messenger, under Settings -> Advanced Settings, you can disable auto-retrieve MMS. By doing so, and not downloading MMS from anyone you don’t trust, you reduce the risk significantly.
- Google Hangouts has a similar option under Settings -> SMS.
- LG’s G4 (for example) using LG’s own Messaging application. Under Settings -> Multimedia Messages, you can disable auto-receive.
- Sony’s Xperia Z3 Messaging app has the same option under Settings, called MMS auto download.
- Samsung’s Messages app has the option under More -> Settings -> More Settings -> Multimedia -> Auto Receive.
The option is likely present on many other SMS apps, but these are the ones we can check immediately.
Android security
Unfortunately this is not the fist time, not is it likely to be the last, that we hear of a potentially damaging security threat to Android. Complicating the issue is the open and distributed nature of Android. You don’t have to look hard to find stories about the Android “f” word, fragmentation. While Google has made significant improvements in the base OS with initiatives like Google Play Services and Android System WebView it is still the case that there are many legacy devices all over the world that are not likely to be patched by their manufacturers – or carriers, in some cases – and do not have these later security improvements in Android.
Google and some OEMs have made a commitment to more regular security focused updates going forward, but this doesn’t mean every phone still in use, or even still on sale, will be included in any such program.
What does it all mean?
- Stagefright is a legitimate security threat to the Android, one which Google and other Android partners have most definitely taken seriously
- Patches are in the wild or in development for many devices
- At present if you are using an Android 4.0 or above device Google believes that you are ‘protected’
- With the information available to date, no one has detected an active exploit of the Stagefright vulnerability in the wild
- Stagefright is NOT limited to MMS attack
Unfortunately this post can not end with a definitive “you’re safe” or “you’re not” conclusion, unless you have a patched device – in which case you should be fine.
Hopefully we’ve been able to provide an understandable explanation of what Stagefright is, how it works and what measures you can take to protect your devices.
Unfortunately, if you are on a pre 4.0 version of Android the likelihood is you may never be sure if you’re at risk from the Stagefright vulnerability if a working exploit is developed in the coming months or years. If this is your situation remember the vulnerability is real and will not disappear for you unless you receive a patch or Google develops a method to patch your system without going through the OEMs and carriers, something they have not been able to achieve with other such vulnerabilities.
It seems unlikely that the Stagefright is the killer vulnerability that will take down Android as a whole but in the coming years it is not inconceivable that we find that it does get exploited somewhere, somehow.
If you want to download the Stagefright Detector App from Zimperium Mobile Security hit the Play Store.
Alternatively you might want to try Lookout Mobile Security’s app.





Nice write up Duncan, very informative.